The easiest way to deploy your App through SSH and Git
SSH deployments usually involve transferring your files via the SSH protocol to a remote server. After that, you can run commands or scripts, for example git fetch or git pull, you can (re)start a web server or database server, etc. All this can be done manually, or you can set up your CI/CD pipeline to automate this process.
If you’re already using a deployment tool like DeployBot, setting up an automated SSH deployment process is easy. Not only can you upload your files through FTP/SFTP, push them to a cloud hosting service like DigitalOcean, Elastic Beanstalk, Heroku, or Amazon Web Services, but you can also connect DeployBot to your server through SSH—allowing you to execute arbitrary shell commands or scripts necessary for your deployment.
In this article we’re going to look at shell deployments. After a brief explanation of SSH authentication methods, I’ll show you how to connect DeployBot to your remote server using SSH keys or passwords, as well as how to trigger shell commands on the remote server.
SSH: Passwords versus Keys
Maybe you’re asking yourself which method is better for user authentication—SSH keys or passwords. Well, that depends, and both authentication methods have their pros and cons. I don’t want to go into a lot of detail here, but let’s take a brief look at the differences:
- SSH Password Authentication: You have a username and a password, and you use this combination to log in to your server. While this is pretty convenient and straightforward for most users, there is a certain risk that somebody sets their password to “123456” or something else which is easy to remember. Generally speaking, simple passwords make this authentication method extremely susceptible to intrusion.
- SSH Public Key Authentication: An SSH key pair consists of a public and a private cryptographic key. The public key is stored on the remote server, and the matching private key is stored on your local computer. The key can be protected with a passphrase, but it’s also possible to set an empty passphrase. Platforms like GitHub, GitLab, etc. support SSH keys to access and write data in your repositories. While this authentication method seems more complicated to set up, it does provide some extra security.
For more information on SSH public key authentication, I recommend this article in the SSH Academy.
If you’ve read this far, you’re probably a DeployBot user and familiar with version control systems, CI/CD, and other related topics. If not, we’ve compiled several beginners' guides: Laravel, Digital Ocean, Ruby on Rails, Docker, Craft CMS, Ghost CMS, Google Web Starter Kit, Grunt or Gulp, Slack, Python, Heroku and many more.
DeployBot uses SSH Keys
When you connect a new GitHub, GitLab, Bitbucket or any other Git repository to DeployBot, a new SSH key pair is being generated, and the private and public keys are automatically installed in the correct locations with the correct permissions. Please note that no passphrase is set for the SSH key in this case.
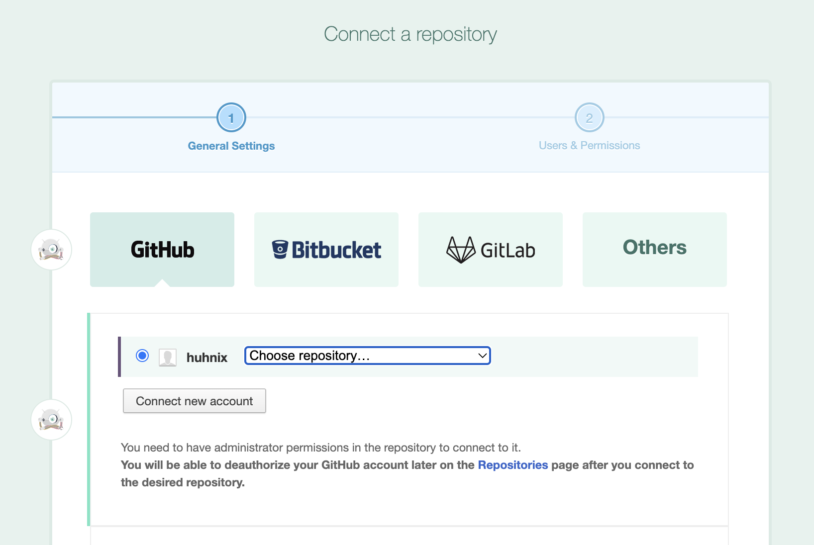
Once your Git repository is initialized, which in most cases takes less than a minute, you should be good to go to create your first deployment environment. Click on Create environment & server to continue.
Setting up Shell Deployment
DeployBot uses deployment environments (represented by one server or a group of servers) to upload your files to. In our case, we’re setting up a “staging” environment, before we configure the actual shell deployment via SSH:
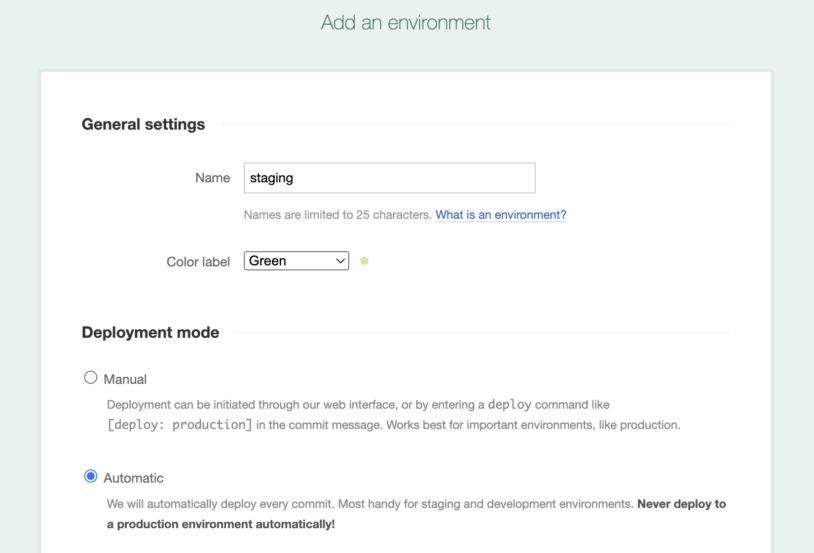
Finally, we are ready to set up a basic shell deployment server with the SSH connection details that we got from our hosting provider:
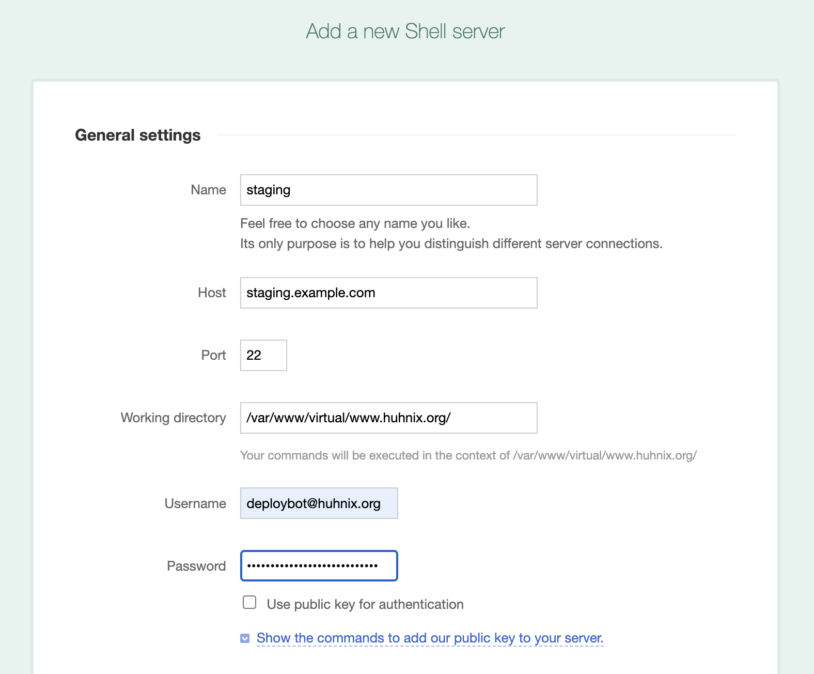
Instead of using password authentication for your remote server, you can activate the checkbox Use public key for authentication. And here comes the most interesting part: DeployBot already has the key to access your Git repository when you gave it the permission before, now that same key will be available in the deployment session when the commands will be run on your server.
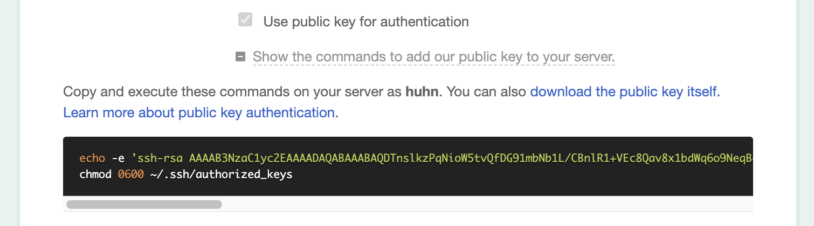
If you click on Show the commands to add our public key to your server, DeployBot displays two commands to execute on your server. All you have to do is copy & paste them and run them in a terminal on the remote machine. At last, click Connect to connect to your server.
SSH Deployments made easy
Remember, that when setting up shell deployments, DeployBot allows you to trigger shell commands on the remote machine—before or after deployment. Simply scroll down in the configuration dialog, tick the respective checkbox, and enter your commands, each command on a separate line.
DeployBot supports several variables which you can use in your shell commands, for example %REPO_NAME%, %BRANCH%, %COMMIT%, and so on. For a complete list of supported variables, have a look at the DeployBot documentation on Shell (SSH) deployments.
With a little magic from the SSH agent forwarding, DeployBot is able to securely forward its key to your server to make your life easier. We really hope you enjoy this simple, but efficient way to deploy.
Happy hacking!
This is an updated version of an article first published on February 27, 2015.






